Linux server ssh 密钥修改
修改 server 段的连接密钥
2023-07-03
注意这里修改的是作为server的密钥,不是用于免密码连接其他服务器的客户端密钥.
# 删除原来的ssh_host_ed25519_key文件
sudo rm /etc/ssh/ssh_host_ed25519_key
# 生成新的ssh_host_ed25519_key文件
sudo ssh-keygen -t ed25519 -f /etc/ssh/ssh_host_ed25519_key
# 其他算法的
sudo ssh-keygen -t rsa -f /etc/ssh/ssh_host_rsa_key
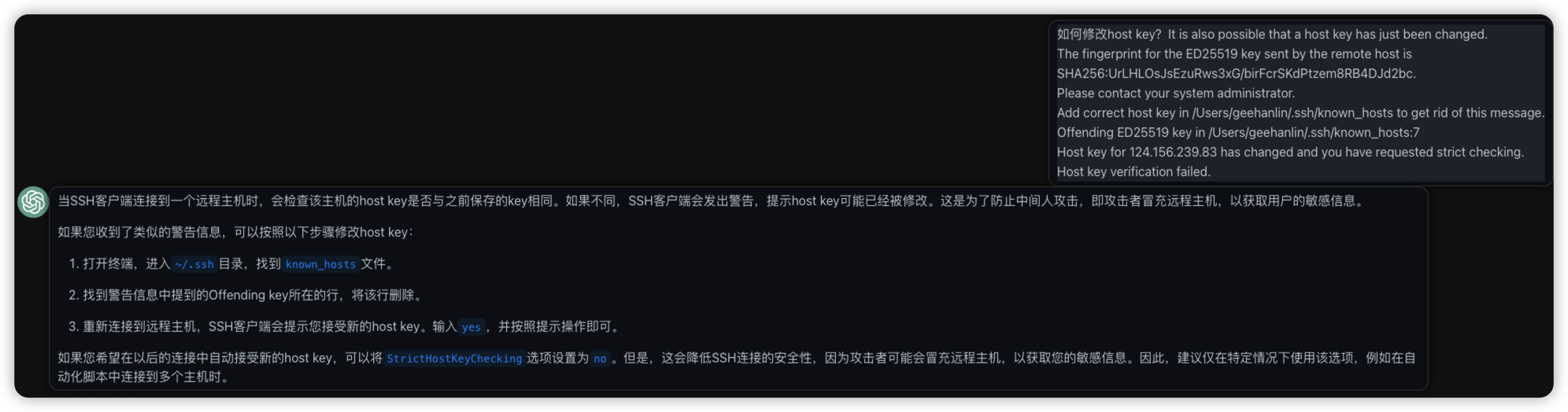
- ssh 连接服务器的时候报错
REMOTE HOST IDENTIFICATION HAS CHANGED
geejp
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ED25519 key sent by the remote host is
SHA256:wrNAeyMZEvOXDnzKi7Oado6NmAXj0HKxycDoW6fllaQ.
Please contact your system administrator.
Add correct host key in /Users/gee/.ssh/known_hosts to get rid of this message.
Offending ED25519 key in /Users/gee/.ssh/known_hosts:7
Host key for 124.156.239.83 has changed and you have requested strict checking.
Host key verification failed.
参考说明修改 ~/.ssh/known_hosts文件, 删除对应host的记录后, 一般就能解决.
但是这次多次删除记录, 每次都还是拿到重复错误的密钥, 无法登录. 只能开始考虑这个密钥从哪里来, 要如何从源头修改了?
- 对比
~/.ssh/known_hosts文件, 发现与另一个host主机的密钥相同
可以看出124.156.239.83主机和43.136.75.92的ssh-ed25519密钥相同
(ocx) ➜ ~ cat ~/.ssh/known_hosts | grep -- 43.136.75.92
43.136.75.92 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMvjnYWupBe5B7B2NB0MpwMtdWu/8elr4PYwOLDD/aLl
43.136.75.92 ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCt2lv2M/cV9NNDPJSebfQ36npJnCcg6gRNQKUM+NS54io1eQDmtyGL4X4CMjLRj9aE578BRfdEKR6wY6BGWP6w6mQB6GYpGxqcaZQokm0Fm9M9wKujYo0Lat8kLdwHu6l/MkigA4YvqQOz1nsr1R9IZTIo1J3kw5j+NQOJcryWC4tsFKKS3jgURX9z7qF82jsfEsGdM3/zOKoBIfnAXNGaywojL/B8ImPseoeZD6zGIDzI0jTb0ikMxPaioLXxW07Oykmsdhyov+KEhk2PdsrKjGOl1qmf4dRyNA+xRX8K1UVTziqZMClGabeI+72eVKcdUs1/EcGrMRpw+BMvnexZgBahap4XrcBP+VtlwTwG+60nzHvV0wEN/JGHj7+0ZtUoaxI55VpzjLL5C6LHLlCPdIVr1+tg772qwdezsqU+9d0THxYdOiI0imHAR5udJK21gGAIGl1NhVQNi0KN2rtpbmC3f449yPVfqdWvh67Ay+gRSigxp2Znvj94JqoWoeM=
43.136.75.92 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPY0C3/c69V0WTXvKYC9dOp1DxnyxrqBGoyOAIzyL1AbvNpgr4NhEYez/bpjdwXVRouh3z8YkOJfPPUXi3ymW0g=
(ocx) ➜ ~ cat ~/.ssh/known_hosts | grep -- 124.156.239.83
124.156.239.83 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMvjnYWupBe5B7B2NB0MpwMtdWu/8elr4PYwOLDD/aLl
(ocx) ➜ ~ vim ~/.ssh/known_hosts
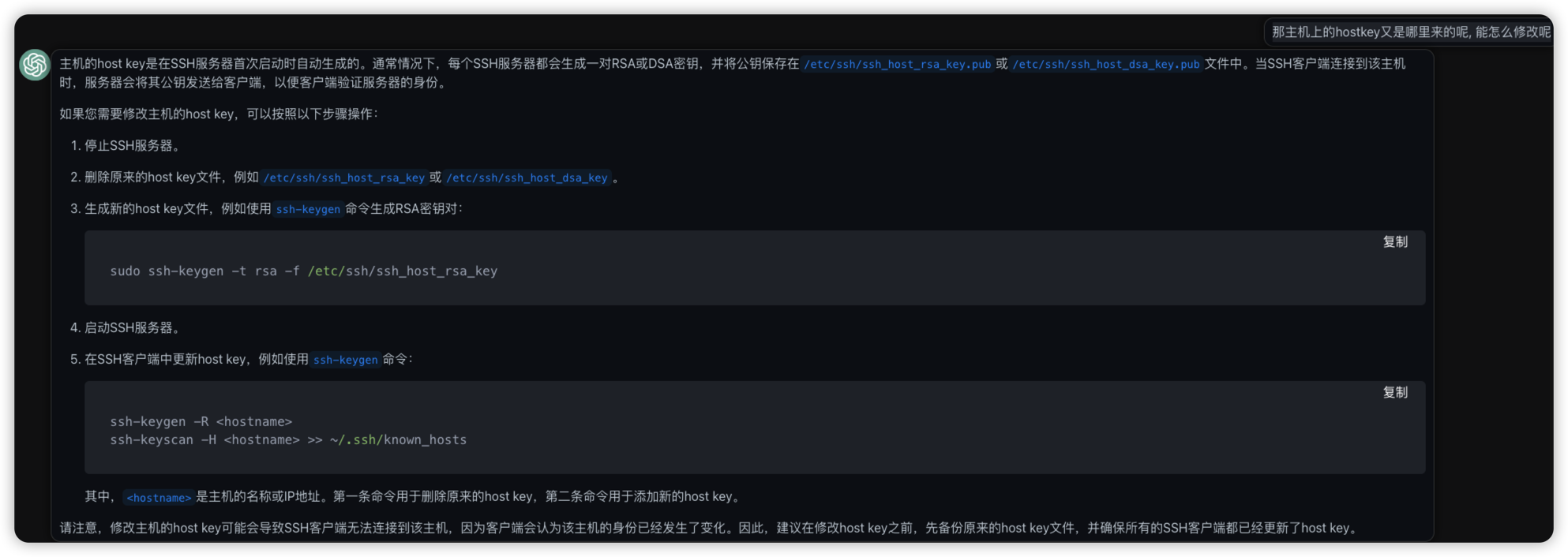
咨询了chatgpt, 才知道这些host的密钥来自于服务器. 在客户端ssh连接服务器的时候, 会获取到服务器的公钥进行保存. 同时服务器上还有密钥用于后续的连接校验, 用于解密客户端的通过公钥加密的信息.
因此对于密钥被多个server使用的解决方法就是到服务器上删除私钥, 重新生成密钥, 同时删除本地~/.ssh/known_hosts对应的记录即可.
至于为什么账号下的两个云服务器会出现两条重复的密钥, 这就得问腾讯云了.
到主机上修改密钥
# 查看ssh文件夹下的一堆公钥
lighthouse@VM-0-4-ubuntu:/etc/ssh$ ls
moduli sshd_config ssh_host_dsa_key.pub ssh_host_ecdsa_key.pub ssh_host_ed25519_key.pub ssh_host_rsa_key.pub
ssh_config ssh_host_dsa_key ssh_host_ecdsa_key ssh_host_ed25519_key ssh_host_rsa_key ssh_import_id
lighthouse@VM-0-4-ubuntu:/etc/ssh$ cat ssh_host_dsa_key.pub
ssh-dss AAAAB3NzaC1kc3MAAACBAPEGrUo9Vx+xoYMmgQvxvTkGiP/D/Os1f8b6msTT38UE3GVlJ3H97FTRrzJ5Q4ydjoDMgy6nqUMGNc6USBgt6OZrHCeFqDjvf7eIlL5g9ypJT9m7ZEyhA15eVv+AK2tNaEfmGAS/xcqwhYMRJ2C7YipkTbCnlV9iYbFd7N9m18jzAAAAFQCb9ytg8KnS31IXy3sxZxjN870sGwAAAIAUzX0NE7hsnErBpGgiUgbdYNrwM6HgQbLeB7PxIvVRRNHXcBpoPxtjCSuflIyTvCxzHDaJ9SGFLMeajX2gcg5witz+rUicb8JJXR7oslu3mmTgxAqmgPyuVGLubeSYZ4LnZ/lv5nA6su5ENcyz1EycOJUI1+QFW/A8zg38qRPiNQAAAIEApkgY/9c7cBmW4C+5vtRmqU0ygrwsQrjllqap7cnDtDwoZNEmsLHuh5iF9MPxEnBpds4zUV5hEB28SNS9kryem6jXGAMOlRPqotPyNmBAqeEQZTf/Q2r5xs9ReZrBCBujMArx/dfNmf40pGp5LgZUNbiEhqXteLZC371x2aUKFAQ= root@VM-0-4-ubuntu
lighthouse@VM-0-4-ubuntu:/etc/ssh$ cat ssh_host_rsa_key.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCkfw3RCMxGH7dx/c1UIjgmV30FOqgfzrqZyen00to1HPFoP0/uj253SqMHNywbMT8QTW2/pQeopXtfhOcMTjxST57zTZlEVbQ4sCwVcL5SHyXh4YEmQlCYi5CfHex02eF+cxqQLIgN9Ra5pSIoeH6qNxWN3n61Ei0acUctkVm5vX3cGfNGFc+ytWY+lgr+6eoNLyxtsnsTxOSjUayFy3vc7m7WyQCWUYAdbBcMAMjIqSm90QLH/O4IvUIdWY2RG4lokkXf3qgYdUsELpxJa+IUARYRoJ6MocQ1e08lsmqba7gXK8ZCshhJZxI5fCjYhVmpr941I0oKfj50ZU58boNH root@VM-0-4-ubuntu
lighthouse@VM-0-4-ubuntu:/etc/ssh$ cat ssh_host_ecdsa_key.pub
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKqH8U270bnoI3f+FP8KZ09tV6Y+2Pai25JIhhIKo11kAf0TCS1qF5ZWBR0cH+rjP9UJwK60Qtkul28AcyezQNg= root@VM-0-4-ubuntu
# 公钥随便都能读取, 私钥只能root账号读写
lighthouse@VM-0-4-ubuntu:~$ ls -alh /etc/ssh/ssh_host_ed25519_key
-rw------- 1 root root 411 May 28 23:43 /etc/ssh/ssh_host_ed25519_key
lighthouse@VM-0-4-ubuntu:~$ ls -alh /etc/ssh/ssh_host_ed25519_key.pub
-rw-r--r-- 1 root root 100 May 28 23:43 /etc/ssh/ssh_host_ed25519_key.pub
# 需要废弃的私钥
lighthouse@VM-0-4-ubuntu:~$ sudo cat /etc/ssh/ssh_host_ed25519_key.pub
ssh-ed25519 FAKE-C3NzaC1lZDI1NTE5AAAAIFV87vdqK/JMfPXSJw3YLizl6fn4ZMAWSInnFfaVD1tf root@VM-0-4-ubuntu
lighthouse@VM-0-4-ubuntu:~$ sudo cat /etc/ssh/ssh_host_ed25519_key
-----BEGIN OPENSSH PRIVATE KEY-----
FAKEbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACBVfO73aivyTHz10icN2C4s5en5+GTAFkiJ5xX2lQ9bXwAAAJguJj7qLiY+
6gAAAAtzc2gtZWQyNTUxOQAAACBVfO73aivyTHz10icN2C4s5en5+GTAFkiJ5xX2lQ9bXw
AAAECN4ZeROgF4mBxmPaizWUmLgv/nOKjnlGrxMhDeOrANM1V87vdqK/JMfPXSJw3YLizl
6fn4ZMAWSInnFfaVD1tfAAAAEnJvb3RAVk0tMC00LXVidW50dQECAw==
-----END OPENSSH PRIVATE KEY-----
# 重新生成密钥
lighthouse@VM-0-4-ubuntu:~$ sudo rm /etc/ssh/ssh_host_ed25519_key
lighthouse@VM-0-4-ubuntu:~$ sudo ssh-keygen -t ed25519 -f /etc/ssh/ssh_host_ed25519_key
Generating public/private ed25519 key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /etc/ssh/ssh_host_ed25519_key.
Your public key has been saved in /etc/ssh/ssh_host_ed25519_key.pub.
The key fingerprint is:
SHA256:fake-eyMZEvOXDnzKi7Oado6NmAXj0HKxycDoW6fllaQ root@VM-0-4-ubuntu
The key's randomart image is:
+--[ED25519 256]--+
| o |
|o = . |
|o.o * +. |
|.+ B @o . |
|=.*.FAKEoS |
|o=o.==.= |
| o+.... |
|.=++ |
|*++o |
+----[SHA256]-----+
# 查看对应的公钥
lighthouse@VM-0-4-ubuntu:~$ cat /etc/ssh/ssh_host_ed25519_key.pub
ssh-ed25519 fake-C3NzaC1lZDI1NTE5AAAAIH1sNumEOYTMFjoZfIjmNca2UpMPYlxgNNFIJs0ag9lp root@VM-0-4-ubuntu
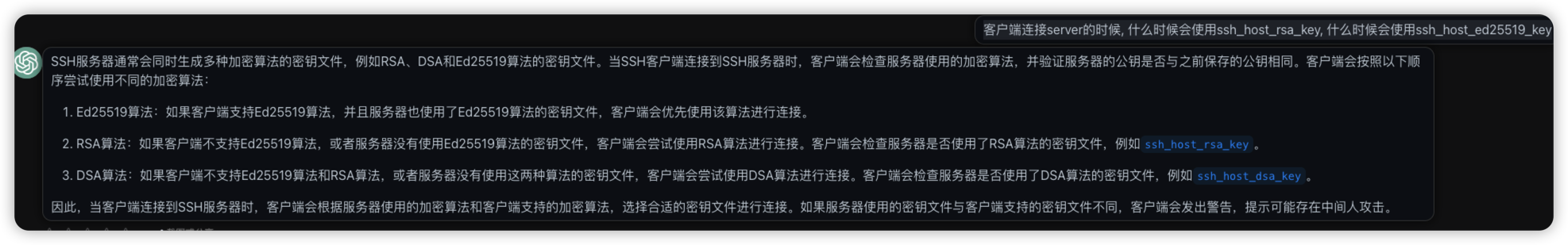
咨询 chatgpt