ranger security zones 安全区域管理
ranger ui界面里有不少security zones的交互, 但是没有使用需求也就没有去了解. 这次阅读ranger的官方文档, 顺便把一些基础功能扫了一遍. 其实security zones有点类似于授权策略里的delegate as admin, 在划分的元数据里进行权限的管理. 每个区域的管理员, 只能管理这个区域的授权信息, 算是大公司里的一个常见需求. 操作步骤首先是对元数据进行划分, 比如按照某几个库某几个表进行拆分, 其次是设置管理员, 然后设置权限即可. 元数据区域的划分需要正交, 也即没有交集.
这套体系对于ranger鉴权本身的逻辑没有什么影响. ranger plugin接收到hive等组件的鉴权请求, 先确定资源属于哪个区域, 如果匹配上的话, 只有这个区域的策略会生效, 再根据具体的库表找到这个区域里的策略, 接下来就是正常的鉴权流程了. audit审计日志里, 会提供具体某个区域的策略生效的信息.
参考文档
Introduction of Security Zones in Ranger
https://cwiki.apache.org/confluence/display/RANGER/Introduction+of+Security+Zones+in+Ranger
This is to introduce a new abstraction in Apache Ranger that would allow carving/bucketing of resources in a service into multiple zones, for better administration of security policies. This would enable multiple administrators to setup security policies for a service – based on the zones to which they have been granted administration rights.
区域里用户角色的划分, 还能区分为操作管理员和审计管理员, 算是挺规范的了.
Zone admin can update only 4 properties in Zone such as :
- Admin Users
- Admin UserGroups
- Auditor User
- Auditor UserGroups
定义区域, 可以根据hdfs路径或是库表进行划分, 要求不同区域彼此没有交集.
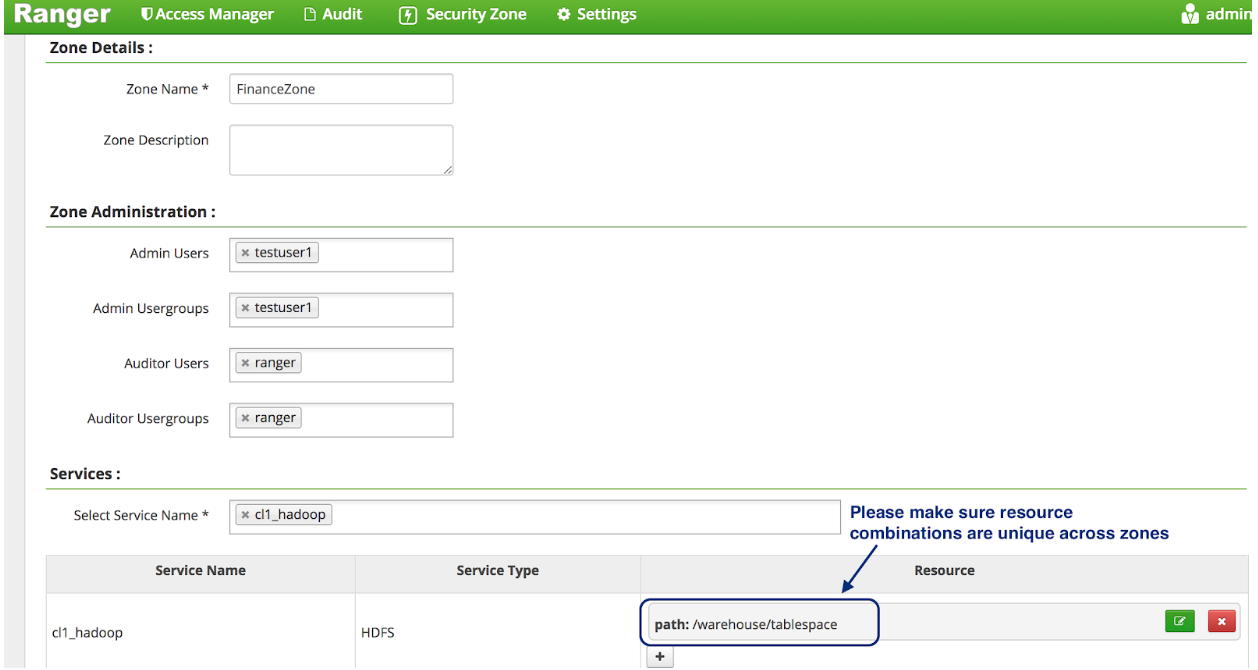
审计信息里, 有具体的区域信息.
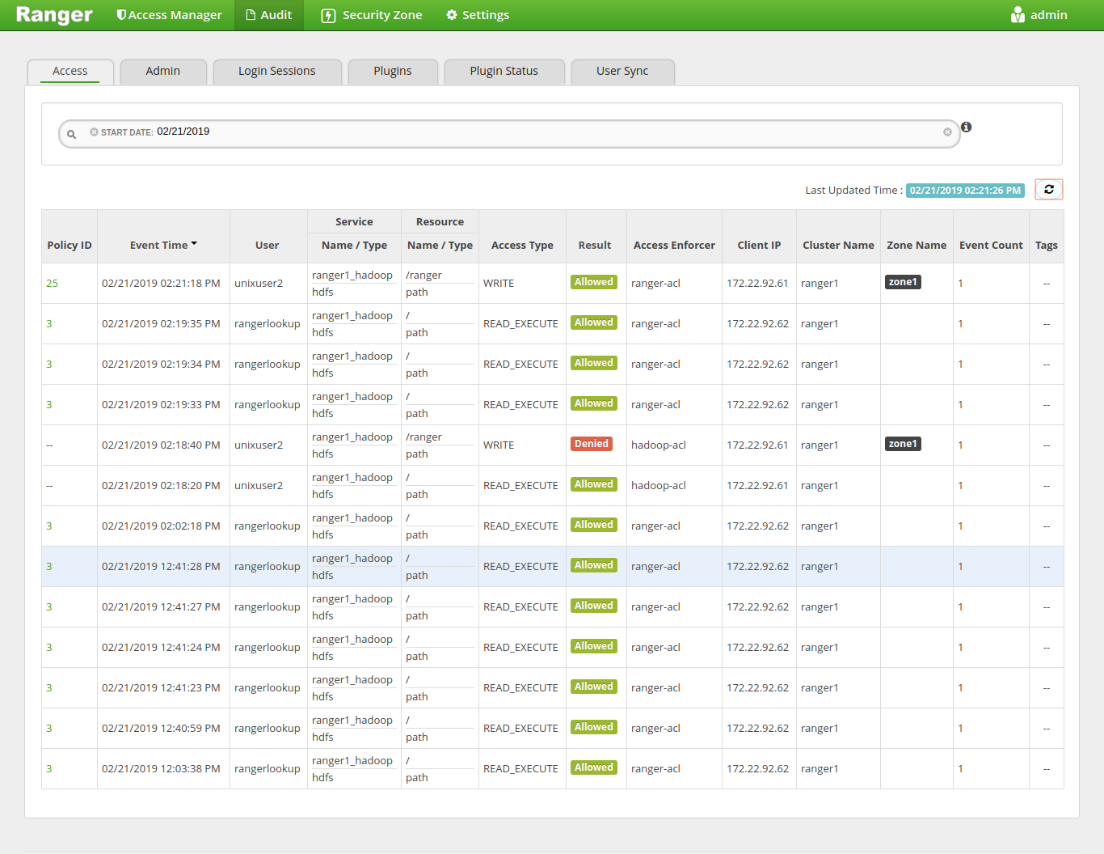
认证流程, 先确定资源属于哪个区域, 如果匹配上的话, 只有这个区域的策略会生效
When a Ranger authorizer plugin authorizes a resource access request, it first determines whether the resource belongs to one of the zones or not. If resource matches a zone, only the policies of the zone are used to authorize the access. If resource does not match any zone, then the policies in the default (unnamed) zone will be used to authorize the access.
For example : two zones are created named as finance and sales
Zone: finance
- service: prod_hadoop; path=/finance/*, /taxes/*
- service: prod_hive; database=finance
- service: prod_kafka; topic=FIN_*
- service: test_hadoop; path=/finance/*, /taxes/*
Zone: sales
- service: prod_hadoop; path=/sales/*
- service: prod_hive; database=sales
- service: prod_kafka; topic=SALES_*
If user Adam tries to access a table belonging to finance database, then RangerHiveAuthorizer will check for all policies defined in service prod_hive for finance zone and allow / deny action based on policies defined in finance zone. If user Adam tries to create a new database named as HRD, then RangerHiveAuthorizer will check for policies defined in service prod_hive for user Adam, as the resource HRD database does not belong to any zone, usual resource based policies will be checked to allow / deny permission to create database.